Ollydbg Program For Mac Os
Cara Mudah Memasukan Serial Number IDM Aktif Selamanya,Cara Jitu Registrasi. Serial Number,dan Kygen Software. Aktif Selamanya Dengan Mudah.siapa sih. Ada dua cara yaitu dengan membeli lisensi dari pembuat software atau meng-crack alias membobol sendiri proteksi software tersebut (bisa juga dengan mendownload crack, keygen, patch atau serial number hasil cracking dari para cracker dunia di.
GarageBand is a fully equipped music creation studio right inside your Mac — with a complete sound library that includes instruments, presets for guitar and voice, and an incredible selection of session drummers and percussionists. 14 programs for 'ollydbg'. Fight Back Against the Latest Threats With ConnectWise Fortify. Advanced Threat Detection & Response by Your Side. Even the best code breaks. It's what it does. But don't let that stop you. Find & fix problems faster with all your telemetry in one place. Membuat Freeware Dengan Excel Membuat When I received it back The software ware told me the serial number was invalid and it. TMPGEnc Authoring Works Version 5 0. 26 crack or serial wanted to test the. Download free download perfect effects dengan cracknya Fast Download. OllyDbg is a shareware, but you can download and use it for free Sep 26, 2011.
Organizations around the world find themselves inundated with security data that is incredibly challenging to digest and process. Servers, endpoint devices, network components, firewalls, cloud services and security appliances all generate massive amounts of information that would be impossible for security analysts to comb through on a daily basis. But this data still has value, and its analysis can yield insights that help improve security. To unlock these insights, many organizations turn to security analytics tools that take on the heavy lifting by correlating data from multiple sources and mining it for crucial security information.
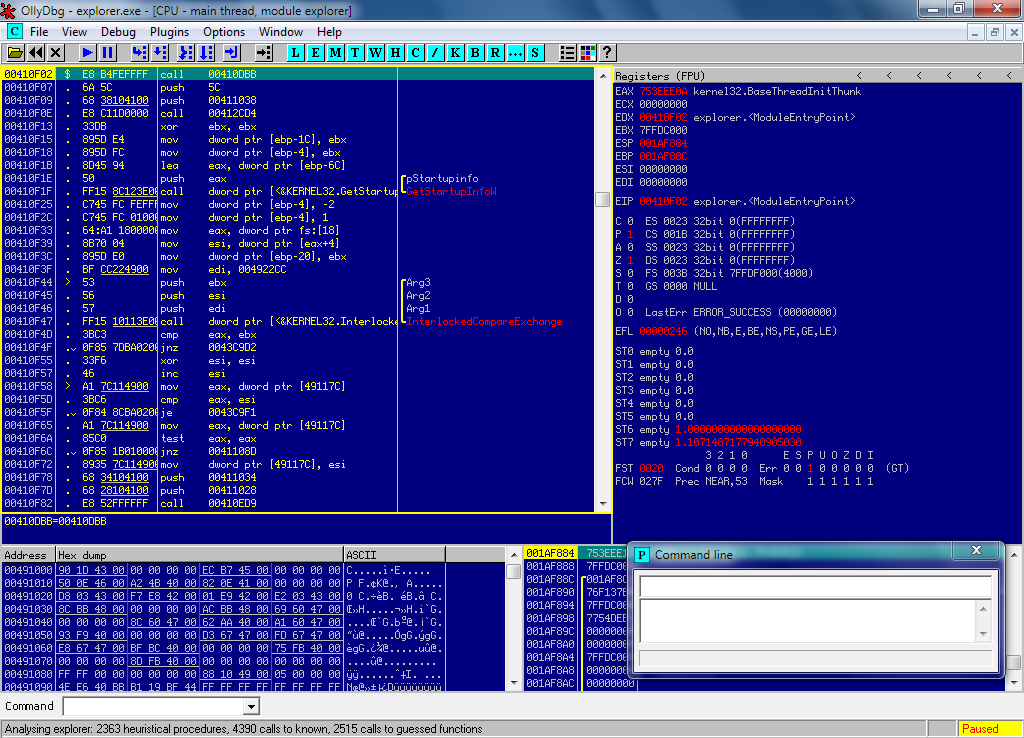
OllyDbg is a 32-bit assembler level analysing debugger for Microsoft ® Windows ®. Emphasis on binary code analysis makes it particularly useful in cases where source is unavailable. OllyDbg is a shareware, but you can download and use it for free. Special highlights are: Code analysis - traces registers, recognizes procedures, loops, API. Mac OS X 10.6 Snow Leopard This program is for advanced users who know how to use it without doing harm to their macs. The authors are not liable for data loss, damages, profit loss or any other types of losses connected with the use or misuse of the program.
My clients are discovering that the same tools that perform security analytics can also be pressed into service for business analytics. The same correlation and analysis engines that generate security alerts may also be tuned to identify business opportunities and deliver added value to the enterprise. That's a powerful argument for security teams seeking to justify added budgets for security analytics. It's difficult to demonstrate the direct return on investment of a security tool, but the case is far stronger when the same tool delivers direct benefit to the business. I'd like to share the stories of two clients who recently deployed the Splunk analytics tool in just this fashion.
Drilling for Oil, and Mining for Security
I'm currently working with an energy company that does natural gas exploration throughout the U.S. and Canada. The company's business model is to bring quite a bit of expensive equipment onto a site, drill for gas and then move on to the next site as quickly as possible. The business relies on sophisticated technology, and the company can't afford to have that equipment sit idle.
It recently deployed Splunk at its sites for security monitoring purposes. Splunk watches over each site's technical and physical security infrastructure, correlating information for signs of potential attack. It simultaneously receives feeds from the site's firewalls and network devices as well as the cameras, doors and gates that make up the physical security infrastructure. If an attacker seeks to gain physical or logical access to the sensitive data stored on-site, the company's security operations center notices immediately and can respond appropriately.
Vin Serial Number Software Free
Organizations around the world find themselves inundated with security data that is incredibly challenging to digest and process. Servers, endpoint devices, network components, firewalls, cloud services and security appliances all generate massive amounts of information that would be impossible for security analysts to comb through on a daily basis. But this data still has value, and its analysis can yield insights that help improve security. To unlock these insights, many organizations turn to security analytics tools that take on the heavy lifting by correlating data from multiple sources and mining it for crucial security information.
OllyDbg is a 32-bit assembler level analysing debugger for Microsoft ® Windows ®. Emphasis on binary code analysis makes it particularly useful in cases where source is unavailable. OllyDbg is a shareware, but you can download and use it for free. Special highlights are: Code analysis - traces registers, recognizes procedures, loops, API. Mac OS X 10.6 Snow Leopard This program is for advanced users who know how to use it without doing harm to their macs. The authors are not liable for data loss, damages, profit loss or any other types of losses connected with the use or misuse of the program.
My clients are discovering that the same tools that perform security analytics can also be pressed into service for business analytics. The same correlation and analysis engines that generate security alerts may also be tuned to identify business opportunities and deliver added value to the enterprise. That's a powerful argument for security teams seeking to justify added budgets for security analytics. It's difficult to demonstrate the direct return on investment of a security tool, but the case is far stronger when the same tool delivers direct benefit to the business. I'd like to share the stories of two clients who recently deployed the Splunk analytics tool in just this fashion.
Drilling for Oil, and Mining for Security
I'm currently working with an energy company that does natural gas exploration throughout the U.S. and Canada. The company's business model is to bring quite a bit of expensive equipment onto a site, drill for gas and then move on to the next site as quickly as possible. The business relies on sophisticated technology, and the company can't afford to have that equipment sit idle.
It recently deployed Splunk at its sites for security monitoring purposes. Splunk watches over each site's technical and physical security infrastructure, correlating information for signs of potential attack. It simultaneously receives feeds from the site's firewalls and network devices as well as the cameras, doors and gates that make up the physical security infrastructure. If an attacker seeks to gain physical or logical access to the sensitive data stored on-site, the company's security operations center notices immediately and can respond appropriately.
Vin Serial Number Software Free
At the same time, the company is also using Splunk to derive business value from this proprietary data. The Splunk analytics engine mines through drilling data and helps the exploration team to quickly identify trends and to project the site's future productivity.
Discovering Healthcare Opportunities and Securing Proprietary Data
Opportunities for analytics also abound in the healthcare field. I'm currently working with a regional healthcare network on its deployment of Splunk's analytics engine as a security solution. The company's IT staff works with vast quantities of sensitive patient information that is regulated by HIPAA. Splunk helps them watch for signs of attack and quickly respond to security incidents, supported by full visibility into their security data.
Ollydbg Program For Mac Free
They've also found ways to deliver direct business value using Splunk. In addition to mining security data, they've turned Splunk loose on economic development records to help identify business opportunities. For example, they recently looked through construction and census data and determined that one area of the city they serve is seeing quite a bit of new home construction and a trend toward young couples moving to the area. They're seizing on this opportunity to build a new pediatric clinic in the area, ready to serve the growing families that the data predicts will continue to move to that part of the city.
It's rare that we're able to find opportunities where security tools can also provide clear business wins. Security analytics is one powerful example of a way that dual-use technology can pay for itself by serving two masters. Bosch me7 tuning software.
This blog post brought to you by:

